Privacy is a right, not a privilege. This article is for web3 developers, founders, and builders who prefer to operate anonymously for a variety of reasons.
The first section of this web3 privacy guide will teach you how to protect your online activity so that you can remain anonymous from third parties and people who would rather track you than mind their own business.
It’s dangerous to be alone, take this advice!

Browser Splitting
The first step is to switch browsers for your crypto-anon identity. You can, for example, use Brave for personal use and Mozilla Firefox for crypto activities.
Why Should You Use a Different Browser?
Because of tracking technology, you should compartmentalize your browsers based on your activity. Tracking technology is primarily used for targeted advertising and can jeopardize your anonymity.

Browser fingerprinting, for example, can collect highly personal information about the websites you visit and your browser configuration, and it's particularly difficult to avoid. You can learn more by reading this study.
Essentially, a website or a third party can instantly connect your anonymous activity with your doxxed activity and store this information, which can then be stolen or doxxed in a data breach (which happens, like, all the time).
Your digital fingerprint is usually sold to advertisers, which means that anyone can buy your entire behavioral profile and online activity, compile the data, and obtain your IRL identity.

How to Protect Yourself Against Browser Fingerprinting
To begin, only use one browser for your anonymous persona and never mix it with other online activities. Set it as your default browser to avoid using your doxxed account to log in to apps and chats.
Then:
- Turn off Javascript (most trackers run on it).
- In your browser's settings, disable tracking scripts.
- Incorporate privacy extensions, such as Privacy Badger, NoScript and Ghostery.
- By default, use Tor or Brave for increased privacy.
- Use this tool from the Electronic Frontier Foundation to test your browser's security.
Tell websites that want to track you to go off and disable cookies in your browser.
 (No, you do not "value my privacy" if you got this banner on your website, because if you really did, you wouldn't need this banner in the first place).
(No, you do not "value my privacy" if you got this banner on your website, because if you really did, you wouldn't need this banner in the first place). Use a private browser and privacy friendly search engines.
Additional Levels of Privacy
You have three other options for enhancing your security setup:
- Create a new account that will only be used for your other activities.
- On your existing computer, install a separate VM (Virtual Machine).
- Use a completely different device for your anonymous persona.

Profiles on Social Media
When networking anonymously, securely managing your social accounts is critical to avoid doxxing yourself or revealing too much about yourself.
Involuntarily Doxxing
Involuntarily doxxing occurs when you doxx yourself and unconsciously reveal cross information that can lead to your doxxed account.
How to Avoid It
First, create an anonymous account with a new email address, and do not log in with the same browser. If you use Twitter, avoid connecting any phone number, or do it by using disposable ones (like Google Voice or a similar service).
Take appropriate action depending on who you’re trying to hide your identity. Your family? Your government? The rest of the cryptocurrency community?
Twitter displays your followers based on the date you began following them, so don't start by following or engaging with your friends or with small accounts, since narrowing your identity will be simple. Always follow big accounts first, and wait a while before engaging with people who can connect you to your real-life identity.

Time Zones
A stalker can use your time zone to pinpoint your exact location. It’s not good for your privacy or security if someone knows your time zone and begins adding clues gleaned from your online activity.
Here's Why You Shouldn't Doxx Your Time Zone
You never know who’s reading and engaging with your content. People become enraged on the internet for reasons you'll never understand or care about. However, it’s especially dangerous when you’re involved in a project and begin to attract competitors and detractors.
Also, if you’re operating in a country where crypto is banned, you should minimize the clues about your location to avoid getting sanctioned. You never know who's monitoring your activity.
To protect yourself and your family, you should avoid giving them any information about your location.

How to Hide Your Time Zone
These are the options available to you:
- On your computer, change the timezone (not really convenient, but works well).
- Avoid posting screenshots of chats because they reveal your timezone.
- Rather than posting immediately, schedule some tweets for when you are sleeping.
- On GitHub, change the
GIT_COMMIT_DATEand/or theGIT_AUTHOR_DATE. - Don’t discuss your surroundings (e.g. weather, political activities, etc).
- Don’t special characters on your keyboard that are specific to your language.
Images and Metadata
Everything you post online contains information about yourself. Always keep this in mind when performing tasks, especially when uploading images.
What Does the Metadata Contain?
Everything, from the camera used to take the photo to the exact location where it was taken.
As an example, consider this image (a glamorous selfie from the author):
 As you can see, I had my geolocation turned on when I took this picture, therefore the GPS metadata is contained in the picture, showing the exact location where it was taken, which is... my home. Oops?
As you can see, I had my geolocation turned on when I took this picture, therefore the GPS metadata is contained in the picture, showing the exact location where it was taken, which is... my home. Oops?
How to Remove Metadata From a Picture
Remove metadata from images before posting, or upload a screenshot instead of the original. On Mac, use the inspector (Preview > Tools > Show Inspector > info box > GPS > « Remove location ») to remove GPS data from any image.
Use Exif Remover or similar websites/apps to remove any remaining data. It should be noted that some websites, such as Twitter, remove the EXIF metadata from images, while others don't.
Link Tracking
Few people are aware that by clicking on a link, they may be revealing their location to a third party. Many internet activities can reveal your IP address. As a result, you should use a VPN or Tor (more on that later).
Instead of Clicking, Copy and Paste
For example, you don't want to click a link and end up logging into an app (like Discord) with the wrong account. Copy and paste any link into the appropriate browser. You will limit tracking, reveal your IP address, and mix social accounts this way.
VPN/Tor: What, How, and Why?
You'd be surprised how often you reveal your IP address on the Internet by clicking on newsletter links, filling out forms, or downloading something.
Not only that, but your internet service provider can monitor your online activity (this is known as ISP tracking). If you live in a country where cryptocurrency is illegal, you'll need to spoof your internet activity with Tor or a VPN.
Tor is a free anonymity service. It focuses on hiding who you are on the Internet. Meanwhile, a VPN only hides what you do and requires payment. While TOR is slower, a VPN is faster.
Choose based on your needs, and if you use both, remember to first connect to Tor before activating the VPN.
Compare VPNs that respect your privacy by limiting the information they collect about you. So far, Mullvad is the only one I'd recommend.
Your Anon Wallet
You'll need funds to get started on web3 with your anonymous persona. If you buy tokens with a credit card, don’t send them directly to your anon wallet because it’lll be easy to link your IRL identity to it. Use Tornado Cash or Monero instead.
How to Use Tornado Cash
Tornado Cash is a decentralized protocol that provides transaction privacy for crypto transfers, and works with the following networks:
Ethereum Mainnet
Binance Smart Chain
Polygon Network
Optimism
Arbitrium One
Gnosis Chain
Avalanche Mainnet
Ethereum Goerli
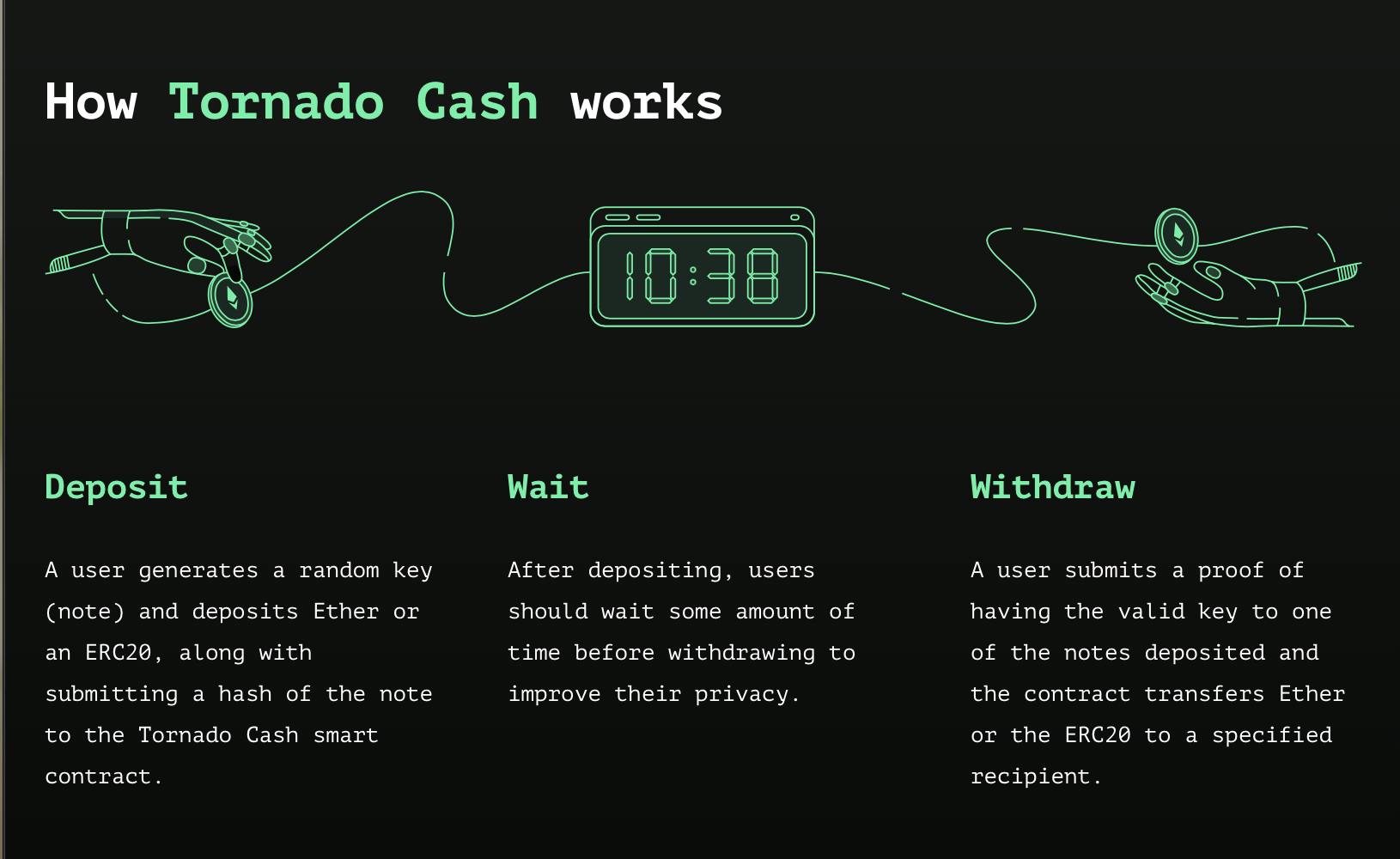
You’ll need to wait before withdrawing your funds, otherwise, it’ll be easy to track the exact amount you deposited and retrieved to another address. Wait between two weeks and a month before withdrawing to your anon address.
Using Monero for Private Transfers
Instead of using Tornado Cash, you can use decentralized finance (DeFi) to convert your funds to Monero and then transfer them to another chain. Monero achieves anonymity by implementing privacy-enhancing technologies that obfuscate transactions. This means that no one can track your Monero activity, even on a public ledger.
However, these methods of achieving privacy are vulnerable to threats and efforts to uncover hidden activities. This constant pressure also provokes communities of privacy-conscious developers to build and patch harder to counter those efforts.
Conclusion: This Is Only the Beginning
Maintaining anonymity is an important task, and it’s also necessary depending on your situation developing on web3.
Developers, founders, and other actors must be able to protect their families and themselves from malicious actions directed at them. Stay safe out there!

This article is a part of the Hashnode Web3 blog, where a team of curated writers are bringing out new resources to help you discover the universe of web3. Check us out for more on NFTs, DAOs, blockchains, and the decentralized future.

